Posts Tagged: cybersecurity
Cybersecurity tips for travel, admin rights available online
Jaki Hsieh Wojan, chief information security officer, has recorded two brief videos that employees may watch at their convenience to learn more about cybersecurity.
One video discusses best practices and general advice for securing devices, such as laptops, when traveling internationally. If you are planning a trip to another country and need to bring work materials, it is a must watch. “Travel Advice with Jaki Wojan” is on YouTube at https://youtu.be/nIviuY5g9_0.
The other video discusses privileged access or administrative rights on local devices. It describes the risks and responsibilities associated with having privileged access, and the process for acquiring those rights. Anyone who wants administrative rights on their device should watch “Admin Rights & Cybersecurity Best Practices with Jaki Wojan” at https://youtu.be/NixotK0SUy4 before submitting a request to IT.
How to spot a phishing email
Phishing emails are the most common way cybercriminals attempt to gain access to an organization's systems. Spam filters will catch many of these emails, but your trained eye can easily spot the rest. Here are some tips to help you spot a phishing email and keep ANR safe from malicious actors.
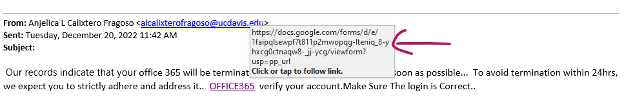
Below is a suspicious email received by an ANR employee this week. The employee noticed the email seemed off and sent it to IT. Great job at spotting the phish!
- Check the sender
This may be a legitimate UC Davis email account, but it seems weird that a random person at UC Davis would send notification of an Office 365 termination to an ANR employee. If there was an issue with an Office 365 account, notification would likely come from ANR's IT – not directly from UC Davis. Additionally, if the email sender is someone you don't know and don't normally communicate with, keep your guard up.
- Subject line
In our example above, the subject line is blank. For an email notifying someone of account termination, there should be a formal subject line. This is a red flag.
- Poorly written
You can often tell if an email is a scam if it contains poor spelling and grammar.
A notification of account termination would be formal and checked for spelling errors and poor grammar. Informal emails on serious subjects containing awkward grammar and misspelled words are likely phishing attempts.
- Suspicious links
Whenever a link is sent in an email, use your mouse to hover over the link to see where it really leads. If a hyperlink address does not match the address text, it is most certainly a phishing attempt.
Use these tips to help identify phishing emails. When in doubt – don't click a link in an email, reach out to IT or your unit director for verification of an email's legitimacy.
IT team rises to challenge of cyberattacks
Update on Accellion data breach
UC was one of more than 100 institutions targeted by a nationwide cyber-attack. As a result, certain university data was accessed without authorization. Protecting the UC community remains the university's top priority. Visit UCnet's Accellion data breach page to learn how to protect yourself, find answers to your questions, and get more information on how you can access free credit monitoring and identity-theft protection.
You can also contact an Experian call center dedicated to the UC breach at (866) 904-6220.
The Substitute Notice of Data Breach was updated on May 21. The FAQs for the Accellion incident are frequently updated so please check https://ucnet.universityofcalifornia.edu/data-security/updates-faq/index.html regularly.
FAQs about the Accellion data breach updated
UC is one of several institutions targeted by a nationwide cyber attack on Accellion's File Transfer Appliance (FTA), a vendor service used for transferring sensitive information. This attack has affected approximately 300 organizations, including universities, government institutions and private companies. In this incident, the perpetrators gained access to files and confidential personal information by exploiting a vulnerability in Accellion's program.
You may register with Experian IdentityWorks for credit monitoring services, using the enrollment code JCZGTC333. If you have already registered, there is no need to take any further action to activate your monitoring.
UCOP has published FAQs in both English and Spanish and is adding to and updating the list as more information becomes available: https://ucnet.universityofcalifornia.edu/data-security/updates-faq/accellion-faq.html. These FAQs address more questions from the community, including questions about the Experian notifications.
UCOP has added recorded webinars about ways people can protect themselves to https://ucnet.universityofcalifornia.edu/data-security/index.html, in both English and Spanish.
UC regards the privacy of all of our community members with the utmost seriousness. We will keep the UC ANR community updated as we learn more and are able to share additional information.