Automatic Deletion of Removed Pages and Assets
During the week of May 6th, 2024, Site Builder will have the Automatic Permanent Deletion of Removed Pages and Assets functionality turned on. It will delete this old removed content from the Site Builder database after it has been 90 days.
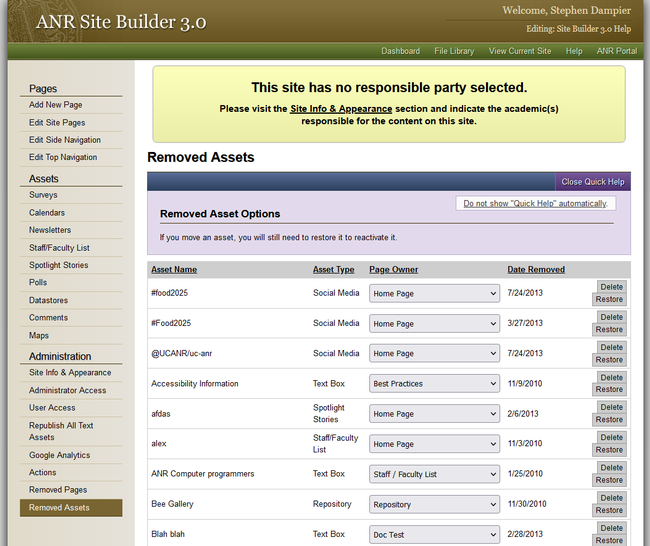
You can see what Pages and Assets have been removed by navigating to the Site Builder Dashboard for your site. In the left hand navigation at the bottom are links for Removed Pages, and Removed Assets.
Please look through the Removed Pages and Assets and backup any content that you might think is important and does not exist elsewhere.
Additional Information on Site Builder Maintenance and Removed Pages and Assets
See Site Builder Administration - Deleted Assets and Pages